KUIPER BELT
- Last Updated:

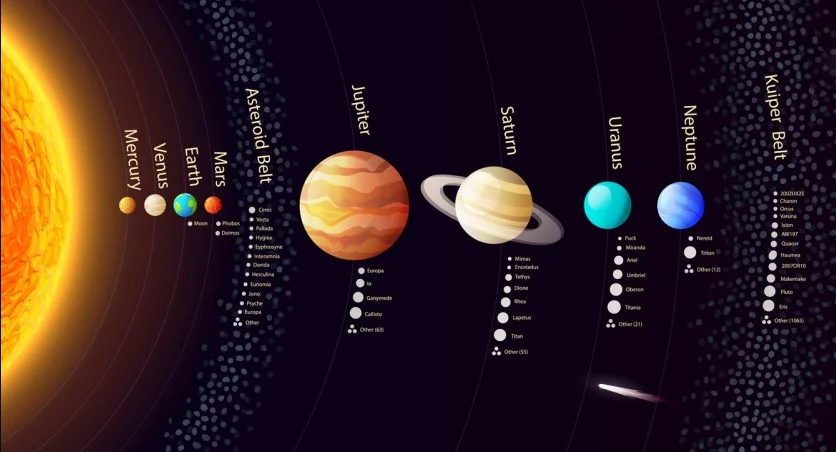
In the outer Solar System this kuiper belt is a circumstellar disc. It is the doughnut shaped region of space beyond Neptune, in the outer edges of our solar system. Millions of icy objects are roaming in this region.
What is Asteroid belt?
The asteroid belt is located roughly between the orbits of the planets Jupiter and Mars as a part of a torus-shaped region in the Solar System.
The asteroid belt lies between 2.2 and 3.2 astronomical units (AU) from the sun. It contains a great many, irregularly shaped solid bodies, of many sizes, but much smaller than planets called asteroids or minor planets. In the Solar System, which is knowns as circumstellar disc also an named as asteroid belt is the smallest and innermost .
Where is Kuiper Belt located?
The inner edge of Kuiper Belt begins at the orbit of Neptune, at about 30 AU from the Sun. (1 AU or astronomical unit measured the distance from Earth to the Sun.) The 1,000 AU is measured the outer edge continues with some bodies on orbits that go even further beyond.
The Main difference
The main difference between the Kuiper Belt and the Asteroid belt is that the Kuiper belt is much larger in size and more massive than the kuiperbelt (that is, it has more objects).
Kuiper Belt is also much farther, nearly 10 times far away from the sun than the Asteroid.
What are the components of Kuiper Belt ?
Kuiper Belt includes bits of rock and ice, comets and dwarf planet. After all s Pluto and a bunch of comets are also included in the family of Kuiper Belt.The interesting thing once again come around when e Eris, Makemake and Haumea.included in their family systems. In the solar systems millions of these icy objects, collectively referred to as Kuiper Belt objects (KBOs) or trans-Neptunian objects.
Who discovered it?
The Kuiper Belt named assigned after the astronomer Gérard Kuiper, who designated a scientific paper in 1951 that speculated about objects beyond Pluto.
However, he didn’t actually discover it. From the time Pluto was discovered in 1930, it would take another 62 years until 1992 for scientists to recognize how populated the region is with objects now called KBOs.
Kuiper was the first one to commenced the idea, and his ideas is well know. For his contribution in this invention his name is attributed all over the region. Some researchers also called it as Trans- Neptunian Region.
How is it Studied?
The work of this Kuiper Belt send image and date from the earth to the space and spacecraft.The first spacecraft to enter the Kuiper Belt region was NASA’s Pioneer 10 spacecraft, when it crossed into space beyond Neptune’s orbit in 1983.
But hat spacecraft didn’t moved to any of the icy worlds in the region. In july 2015 the first spacecraft to actually visit an object in the Kuiper Belt was NASA’s New Horizons, which flew by Pluto and its moons.
Why is it important?
When the scientists studied about Kuiper Belt, the most important aspects to the Kuiper Belt is that it comes under our solar system. Studying this the researcher could know how planets and planetesimals are working – the building blocks of the planets formed and lots more.
About the ancient Kuiper Belt object Arrokoth (2014 Mu69), has send data by the New Horizons spacecraft. The data send by the New Horizons spacecraft. Include data like fossils reveal the formation of life on earth and objects such as Arrokoth show how planets formed in space.
The Kuiper Belt is a region we’re still beginning to explore and our understanding is still evolving.
Key Vulnerbilities Which Ethical Hackers check for :
- Injection attacks
- Changes in security settings
- Exposure of sensitive data
- Breach in authentication protocol
- Components used in the system or network used as access points
TYPES OF HACKERS
- Black hat hacker
- Grey hat hacker
- White hat hacker
BLACK HAT HACKER VS WHITE HAT HACKER
Black hat hackers are cybercriminals who hacks the computer of an individuals and stole all confidential resources and do the vulnerabilities and exploit them for malicious reasons or financial gain. The hackers get unauthorized access to systems and make harm their operations or steal sensitive information.
White hat hackers are cybersecurity expert who are certified to hack organizational networks and computer systems. They are well trained enough to find vulnerabilities in systems.

Skills Required to become an Ethical Hacker
- Knowledge of programming
- Scripting knowledge
- Networking skills understanding of databases
- Knowledge of hacking tools
- Knowledge of search engines and servers
- Knowledge of multiple os
Ethical Hackers work within an office setting and are confined mostly to server rooms. There are no fixed working hours. There could be a situation where they might need to work long hours. They work both as freelancers and employees.
The job entails high work pressures and the responsibility of Ethical Hackers ranges from extracting a bug in the IT environment to making the IT environment stronger against external threats. They are hired by Governments, IT security firms, financial institutions, telecom companies, hospitals etc.
ROLES AND RESPONSIBILITIES
- An ethical hacker must seek authorization from the organization that owns the system.
- Determine the scope of their assessment and make known their plan to the organization.
- Report any security breaches and vulnerabilities found in the system or network.
- Keep their discoveries confidential.
- Erase all traces of the hack checking the system for any vulnerabilities.
Career Path to become an Ethical Hacker
To pursue a career in ethical hacking one should opt for the science stream with Physics, Chemistry, Mathematics and Computer Science for Btech., BE. or BSc. in Computer Science/ IT Engg. You could also enroll in a professional course in cyber security and EH training programs.
It is also beneficial to master the trending programming languages like C, C++, Python, Java, Ruby, Perl etc. and get professional certification in the field of CISSP, TICSA, Security +, Cloud computing, Risk Management and Application Development. The CEH course is also highly recommended.
Besides these, a thorough knowledge of cryptography, analytical and logical thinking, keen observational skills, ability to work with fine details and problem- solving attitude fine-tunes the profession. The average salary ranges from Rs 6 lakh to 20 lakh per annum. It is one of the most sought-after careers in recent times.
Also Read : THE WOOLLY MAMMOTH


